Managing package dependencies with Yarn and Node Security
Nov 10, 2017 using tags nodejs, reactjsYarn has been a great alternative to npm and we’ve been using it at Switchboard for quite a while.
You can get a bird’s eye view of the packages that have updates available using
yarn outdated. As you might expect, it will check each dependency in your
package.json file for newer upstream versions.
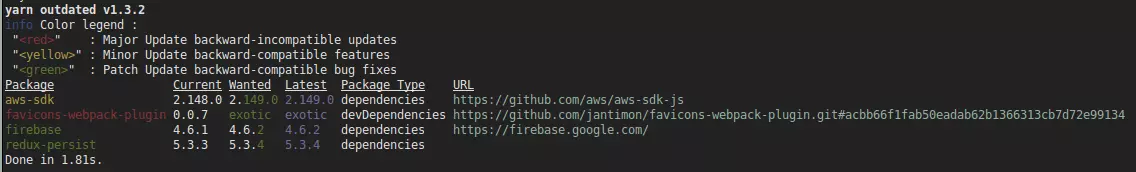
From the above snippet you can see that there is a newer version of the
aws-sdk package. Yarn allows you to interactively step through your
dependencies and update packages individually. This is done via yarn
upgrade-interactive --latest, which also takes care of updating the version
numbers in your package.json file.
Transitive Dependencies
It is also a good idea to occasionally update your transitive dependencies.
Yarn unfortunately does not have a straight-forward way of getting this done.
The “trick” here is to blow away your lockfile and do a fresh yarn install.
$ rm yarn.lock && yarn installThis approach assumes that your package.json file is the source of truth for
your core dependencies and that it’s updated whenever your core dependencies
are updated (using the technique mentioned initially).
As always, test your app thoroughly between dependency updates to make sure nothing breaks!
Vulnerability Scanning
Node Security checks all your dependencies for known vulnerabilities and also easily incorporates into your build/CI pipeline.
$ yarn add --dev nsp nsp-preprocessor-yarnAdd it as a script target to your package.json file:
"scripts": {
// ...
"security-check": "nsp check --preprocessor yarn --reporter table"
},Then run it locally or as part of your CI build using yarn run
security-check:
You should ensure that your CI system runs this security check at least once
a day. If you need to temporarily add nsp exceptions, you can do so by adding
the advisory link URLs to your project’s .nsprc file.
{
"exceptions": [
"https://nodesecurity.io/advisories/525",
"https://nodesecurity.io/advisories/526",
"https://nodesecurity.io/advisories/527",
"https://nodesecurity.io/advisories/534",
"https://nodesecurity.io/advisories/535"
]
}